

UPDATE June 6, 2018: Cleaner patch test results paint a clearer – and brighter – picture
Since first presenting this research at the HITB conference on April 13, 2018, we have been having very constructive discussions with parties throughout the Android ecosystem. These constructive conversations have not only helped vendors spot past oversights and improve patching processes, but also helped us spot shortcomings in our own assumptions and analyses. The feedback has enabled us to improve the Android patch analysis in three primary areas:
- Differentiate community builds from official builds. Many community firmware builds have significantly larger patch gaps than the vendors’ official builds (and a few are doing better than the vendors), skewing the patch averages. We are now distinguishing community builds and present these separately in our statistics.
- Removed unreliable tests from the test suite. Some of our earlier patch tests were written based on naïve assumptions that vendors would apply security patches without modifications. Sometimes vendors do change patches, often for good reasons. Tests that resulted in “patch not present” results for modified patches have been removed from the active test suite.
- Corrected applicable patch date and relevant Android versions. While it is usually clear which Android versions and patch level date a given security patch applies to, there have been cases where we simply got it wrong. (Sorry, Samsung!) We have done our best to correct all such errors and ensure all tests are flagged with the correct Android versions and patch level date.
We regret that errors resulting from these shortcomings led us to initially report an Android patch gap larger than it really is. This mistake turned out to be especially unfair to vendors whose actual patch record is exceptionally good. The few false positives, some of which applied only to specific vendors, had a disproportionate negative impact on their otherwise stellar average.
At the same time, we are honored that our tools are helping teams around the globe to detect and address oversights in their patching processes, measurably so. Thank you to the vendors for our constructive discussion and thank you to the community for using SnoopSnitch for spotting patch gaps.
The Android ecosystem contains a hidden patch gap
Android is the most successful operating system to date, with two billion devices in active use. With success comes responsibility, in this case for the security and privacy of mobile users all over the world. One central pillar of keeping these devices secure is providing regular patches.
Android has had its difficulties with patching in the past, with only 17% of devices operating on a recent patch level in 2016. Since then, many device vendors have improved their patching frequency: Phones now receive monthly security updates.
Installing patches every month is an important first step, but is still insufficient unless all relevant patches are included in those updates. Our large study of Android phones finds that some Android vendors regularly miss patches, leaving parts of the ecosystem exposed to the underlying risks.
Android vendors differ in their patch completeness:
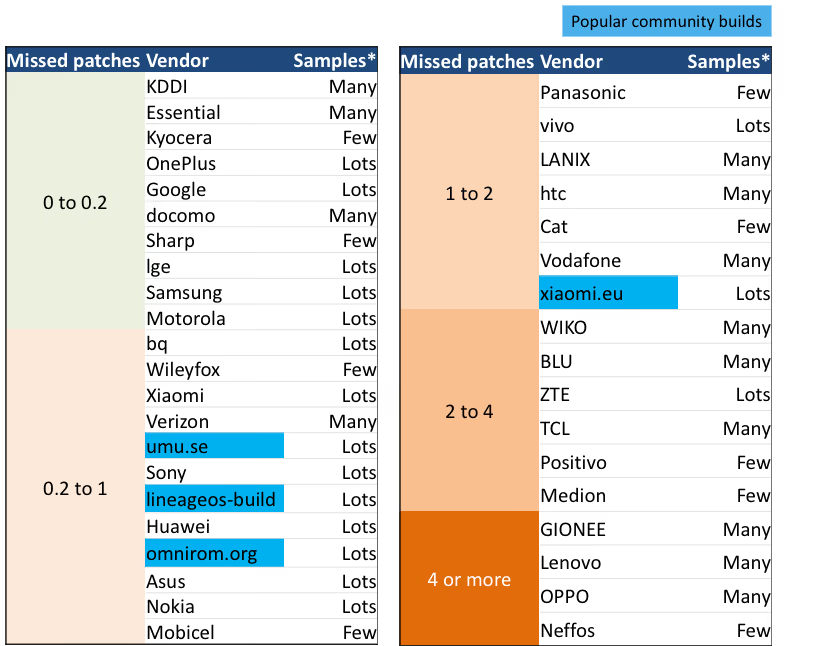
Notes– The table shows the average number of missing Critical and High severity patches before the claimed patch date* Samples – Few: 5-9; Many: 10-49; Lots: 50+– Some phones are included multiple times with different firmware releases– Not all patch tests are always conclusive, so the real number of missing patches could be higher– Not all patches are included in our tests, so the real number could be higher still– Only phones are considered that were patched January-2018 or later– A missing patch does not automatically indicate that a related vulnerability can be exploited
[Data current as of June 6, 2018. Check this blog post from 2020 for an update.]
Android exploitation is still hard Modern operating systems include several security barriers, for example ASLR and sandboxing, all of which typically need to be breached to remotely hack a phone. Owing to this complexity, a few missing patches are usually not enough for a hacker to remotely compromise an Android device. Instead, multiple bugs need to be chained together for a successful hack.
The criminal ecosystem seems to understand the challenges in hacking Android phones. Instead of exploiting known software vulnerabilities, criminals focus on social engineering users into installing malicious apps, often from insecure sources, and then granting excessive permissions to these apps. In fact, hardly any criminal hacking activity has been observed around Android in 2017.
That leaves state-sponsored and other persistent hackers, who usually operate stealthily. These well-funded hackers would typically resort to “zero day” vulnerabilities but may also rely on known bugs to develop effective exploit chains. Patching known bugs hence increases the effort for these very determined hackers.
Be aware of your Android patch level
As Android is ever increasing in popularity, the hacking incentives will only keep growing, as does the ecosystem’s responsibility for keeping its users secure. No single defense layer can withstand large hacking incentives for very long, prompting “defense in depth” approaches with multiple security layers. Patching is critically important to uphold the effectiveness of the different security layers already found in Android.
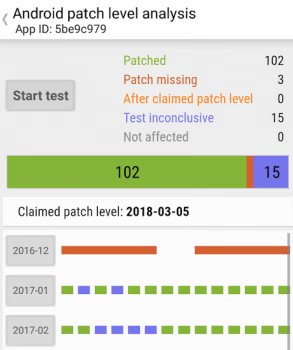
Now that monthly patches are an established baseline for many phones, it’s time to ask for each monthly update to cover all relevant patches. And it’s time to start verifying vendor claims about the security of our devices. You can measure the patch level of your own Android phone using the free app SnoopSnitch.
References
Details of this research were presented at the HITB conference](https://conference.hitb.org/hitbsecconf2018ams/sessions/mind-the-gap-uncovering-the-android-patch-gap-through-binary-only-patch-level-analysis/) on April 13, 2018, in Amsterdam and at AsiaSecWest on June 6, 2018 in Hong Kong. [Slides.